Contents
Introduction
Azure Web Application Firewall (WAF) on Azure Front Door (AFD) is a global and centralized solution to protect web services against common malicious attacks and vulnerabilities before they enter the virtual network environment. AFD WAF implementation enables services to be substantially available and thereby eliminating any compromise on performance. A WAF policy easily links to any Front Door profile and new rules can be instantly deployed to respond quickly to changing threat patterns.
Azure Front Door has two tiers: Front Door Standard and Front Door Premium. WAF is natively integrated with Front Door Premium with full capabilities. For Front Door Standard, only custom rules are supported.
IIS Level Changes
To determine the health and proximity of each backend for a given Azure Front Door environment, each Front Door environment periodically sends a synthetic HTTP/HTTPS request to each of your configured origins. Azure Front Door then uses these responses from the probe to determine the "best" origin to route your client requests.
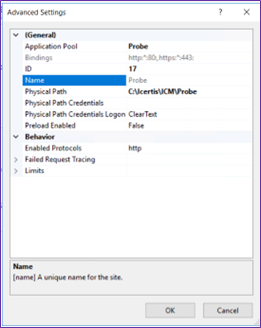
Probe Website
Identify the tenant
For example, the Tenant below is identified based on client configuration either ST or MT, and so on.
VM:
- NewCoreMT1
- NewCoreMT3
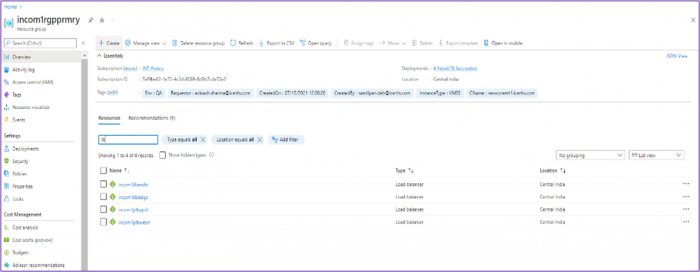
Identify the Resource Group – Login to the Azure portal
Resource groups:
- Incom1rgpprmry
- Incom3rgpprmry
Identify the VM
1. Go through all Resource groups and VMSS to identify the underlying VM.
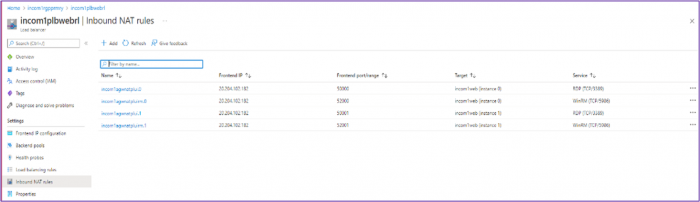
2. Navigate to Loadbalancer > Inbound Nat Rule to identify a Public Port.
3. Select Inbound NAT Rule from the left side menu.
Probe website
Perform the following steps on each VM
1. VM from newcoremt1 resource group incom1rgpprmry
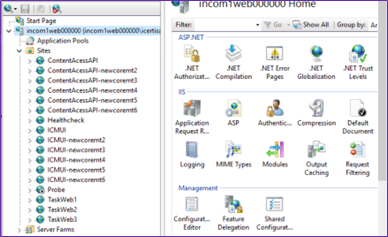
2. Go to IIS and create a new web site named Probe if the “Health check” web site is not present.